Common Control Frameworks and SASE
How does SASE align to a framework like SASE? Let's explore!
John Spiegel
6/11/20242 min read


It's true that all of us in cybersecurity enjoy a good framework. Why? We must oversee, protect, and understand an area that is complex and difficult to process. As security extends across the enterprise from basic physical elements like a building to the complexity of interactions of a container-based application, having a framework provides a map to understand the multi-layered mosaic that covers all aspects of the business. Using structures such as NIST, ISO 27001, or CIS brings clarity and understanding to new and old technologies and operating models. The difficulty becomes understood. It allows us to speak a common language or, even better, use a topographical map to understand the landscape.
New technologies present new challenges. How do they map into various frameworks? For instance, if I am deploying a platform such as Service Access Security Edge (SASE), how does it fit into a standard like CIS? First of all, SASE is a framework in itself. It covers network elements and a security stack to deliver applications to an edge device in a branch office or a remote worker. It supports both legacy applications in the private data center as well as next-generation cloud-based applications such as SaaS (for example Workday or O365). Given the breadth of SASE, what does the map look like?
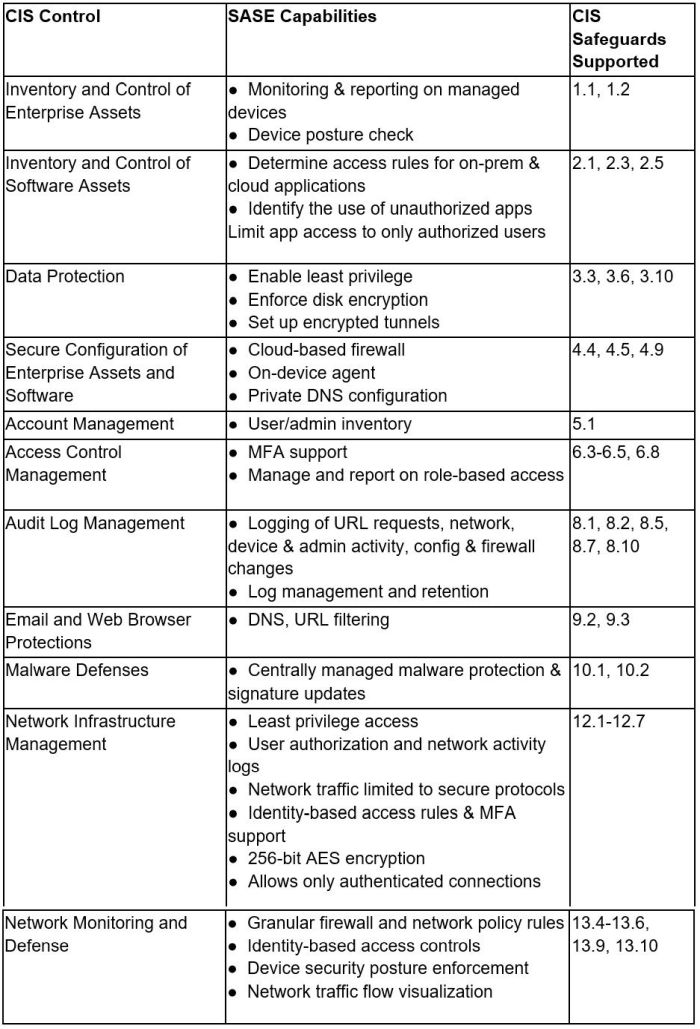
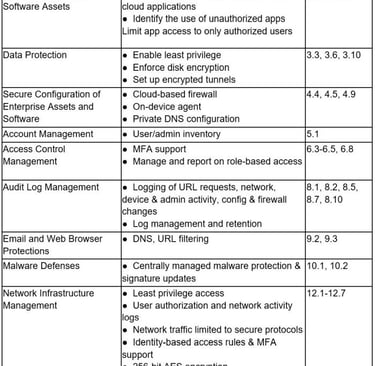
For CIS, let's use version 8, which came out in 2021. Enhancements include cloud-based computing and virtualization, which critically account for the rise in work-from-home. Changing attack patterns prompted the update. Each area is called out as a "Safeguard."
How does SASE map out?
As SASE brings to the table security tools such as ZTNA, CASB, SWG, FWaaS, DLP and leverages identity, the results are positive. 35 controls are covered!! In addition to covering these controls, the SASE framework also provides security tool consolidation, integration between solutions, lower KTLO, and if done right, a strong ROI for the company.
If you are not considering a transition to SASE, you should. Making the migration will provide faster application performance and security improvement and make that conversation with the outside auditor easier. Plus it will help you understand the complexities of edge networking and security!!